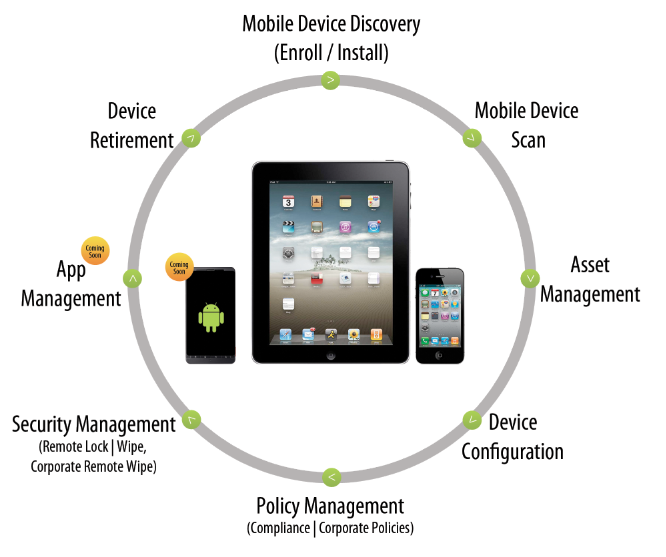
IT departments are now under pressure because they are the result of the best options for your business in terms of mobile device management (MDM). IT services more than ever aware of the risks that are presented devices their employees when it comes to security vulnerabilities and other phishing. As
a result, IT administrators are interested in learning more security threats to stop them in their tracks, and not how they react.
The program is designed to prevent such attacks, it is, but there are other solutions MDM untangle the mess when it happened to strive for. It is simply too late in some cases, particularly when the data has a high risk. Mitigation can help to a certain extent, but if the security in environments where Bring your own device was wounded (BYOD) is the norm, in many cases, it is too little, too late.
Part of the problem is that we're not just talking about the mobile devices, but also on the desktop and the changes due to the introduction of MDM solutions with a workforce that will use their own equipment.
Mac brings its own problems, who are taking action as part of their BYOD, but do not update their systems expertise to other platforms, make sure that they are protected. In such cases, management is sometimes forced to ask their employees to apply for jobs usually take an IT department ... IT consumer since it is a widespread problem.
What actions are performed usually for IT departments when there is a crisis, making them prone to sensitive information about the equipment office?
1 Determine the extent of the problem, showing how many versions of the software that is vulnerable and there is no work.
2 Turn off the software, or if possible upgrade.
3 Let them know what they need to more regularly update the user and make sure that the emergency measures will be needed in the future.
These actions are only relevant if the IT services and access control devices that are used throughout the organization. When the size of the organization with its own hardware, the second stage can not be done.
In these cases, the most important, but not access to the software ... the ability to access and possibly quarantine devices whose security has been violated is the key to successful management of BYOD.
So while your employees can make a lot of their IT management with regard to their personal devices, the latest call to action comes from the IT department. It is here that the policy should be clear that employees should be aware that participating in the BYOD responsible for regular updates and security measures are taken and that management may, at times, the nearest approach the device when the breach must be sufficiently serious.
Thus, the relationship between IT and the users of the equipment is not the same as it was before. The balance has changed with the growth of BYOD trend, and the two sides should work together to find a solution for each MDM safe device for business and personal purposes.
The author has many years of experience in blue chip organizations and professional wide range of issues, including software development, project management and mobile device management (MDM) is written between the growing trend of Bring-Your-own-device (BYOD).
The program is designed to prevent such attacks, it is, but there are other solutions MDM untangle the mess when it happened to strive for. It is simply too late in some cases, particularly when the data has a high risk. Mitigation can help to a certain extent, but if the security in environments where Bring your own device was wounded (BYOD) is the norm, in many cases, it is too little, too late.
Part of the problem is that we're not just talking about the mobile devices, but also on the desktop and the changes due to the introduction of MDM solutions with a workforce that will use their own equipment.
Mac brings its own problems, who are taking action as part of their BYOD, but do not update their systems expertise to other platforms, make sure that they are protected. In such cases, management is sometimes forced to ask their employees to apply for jobs usually take an IT department ... IT consumer since it is a widespread problem.
What actions are performed usually for IT departments when there is a crisis, making them prone to sensitive information about the equipment office?
1 Determine the extent of the problem, showing how many versions of the software that is vulnerable and there is no work.
2 Turn off the software, or if possible upgrade.
3 Let them know what they need to more regularly update the user and make sure that the emergency measures will be needed in the future.
These actions are only relevant if the IT services and access control devices that are used throughout the organization. When the size of the organization with its own hardware, the second stage can not be done.
In these cases, the most important, but not access to the software ... the ability to access and possibly quarantine devices whose security has been violated is the key to successful management of BYOD.
So while your employees can make a lot of their IT management with regard to their personal devices, the latest call to action comes from the IT department. It is here that the policy should be clear that employees should be aware that participating in the BYOD responsible for regular updates and security measures are taken and that management may, at times, the nearest approach the device when the breach must be sufficiently serious.
Thus, the relationship between IT and the users of the equipment is not the same as it was before. The balance has changed with the growth of BYOD trend, and the two sides should work together to find a solution for each MDM safe device for business and personal purposes.
The author has many years of experience in blue chip organizations and professional wide range of issues, including software development, project management and mobile device management (MDM) is written between the growing trend of Bring-Your-own-device (BYOD).